Phishing campaigns target universities amid Omicron
Cybersecurity researchers have identified an increase in email phishing targeting mostly North American universities attempting to steal university login credentials. The threats typically leverage COVID-19 themes, including testing information and the new Omicron variant. Researchers believe activity will increase in the next two months as colleges and universities provide testing for students, faculty, and other workers traveling to the United States during the holiday season. The phishing emails contain attachments or URLs for pages intended to harvest credentials for university accounts. The landing pages typically imitate the university’s official login portal.
Emails use subject lines such as “Attention Required – Information Regarding COVID-19 Omicron Variant” or “Covid Test,” and in some cases included file attachments titled “Covid-19_Test-Results.htm”
Read more about the details of the campaign here.
What can you do?
-
Be extremely cautious with emails that match the subject line or attachment descriptors above.
-
If you receive an email matching the above descriptors and you believe it to be a phish, please please report it to Google by following the instructions here.
-
Since this campaign has impacted North American universities, we ask that you also report it to IT by entering a ticket at TechHelp.fitnyc.edu or by forwarding it to [email protected] so that we can notify appropriate security authorities.
-
-
When visiting the MyFIT portal from a link, look for the padlock icon to the left of the URL in your browser. Never enter your credentials if this padlock is missing. This could be an indication that you have landed on a fake site.
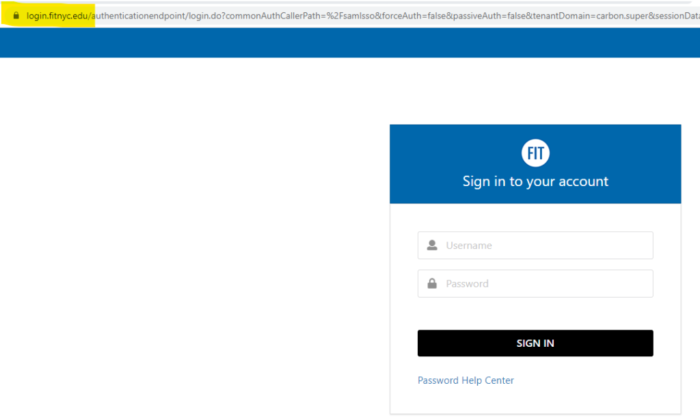
-
If you have not already, we encourage you to enable Two-Factor Authentication (2FA) on your FIT Google account. Also referred to as 2-Step Verification, it remains the best way to secure your data if your credentials are stolen.
-
Like with any email, always question the source and follow our four don’ts of email safety.
